TLS Security Policies
When your deployed business needs to provide services for internet users, HTTPS encryption is generally used to ensure the secure transmission of data. For the HTTPS scenario, the security policy function provides the ability to configure the minimum version of the TLS protocol and the encryption algorithm suite. When creating and configuring HTTPS listening, you can bind your own security policy to ensure the security of your business and achieve the necessary security requirements.
Predefined Policies
Predefined policies cannot be edited or deleted. The encryption suites and TLS protocols supported by the current eight predefined policies are shown in the following table.
| Policy Name | Minimum TLS Protocol Version | Supported Encryption Suite |
|---|---|---|
| Native Policy | TLSv1 | OpenSSL syntax format ALL:!NULL:!aNULL:!DSS:!RC4:!RC2:!EXP:!LOW |
| TLS minimum version 1.2, high security | TLSv1.2 | ECDHE-ECDSA-AES128-CCMECDHE-ECDSA-AES128-CCM8ECDHE-ECDSA-AES128-GCM-SHA256ECDHE-ECDSA-AES128-SHAECDHE-ECDSA-AES128-SHA256ECDHE-ECDSA-AES256-CCMECDHE-ECDSA-AES256-CCM8ECDHE-ECDSA-AES256-GCM-SHA384ECDHE-ECDSA-AES256-SHAECDHE-ECDSA-AES256-SHA384ECDHE-ECDSA-CHACHA20-POLY1305ECDHE-RSA-AES128-GCM-SHA256ECDHE-RSA-AES128-SHAECDHE-RSA-AES128-SHA256ECDHE-RSA-AES256-GCM-SHA384ECDHE-RSA-AES256-SHAECDHE-RSA-AES256-SHA384ECDHE-RSA-CHACHA20-POLY1305 |
| TLS minimum version 1.1, high security | TLSv1.1 | ECDHE-ECDSA-AES128-CCMECDHE-ECDSA-AES128-CCM8ECDHE-ECDSA-AES128-GCM-SHA256ECDHE-ECDSA-AES128-SHAECDHE-ECDSA-AES128-SHA256ECDHE-ECDSA-AES256-CCMECDHE-ECDSA-AES256-CCM8ECDHE-ECDSA-AES256-GCM-SHA384ECDHE-ECDSA-AES256-SHAECDHE-ECDSA-AES256-SHA384ECDHE-ECDSA-CHACHA20-POLY1305ECDHE-RSA-AES128-GCM-SHA256ECDHE-RSA-AES128-SHAECDHE-RSA-AES128-SHA256ECDHE-RSA-AES256-GCM-SHA384ECDHE-RSA-AES256-SHAECDHE-RSA-AES256-SHA384ECDHE-RSA-CHACHA20-POLY1305 |
| TLS minimum version 1.0, high security | TLSv1 | ECDHE-ECDSA-AES128-CCMECDHE-ECDSA-AES128-CCM8ECDHE-ECDSA-AES128-GCM-SHA256ECDHE-ECDSA-AES128-SHAECDHE-ECDSA-AES128-SHA256ECDHE-ECDSA-AES256-CCMECDHE-ECDSA-AES256-CCM8ECDHE-ECDSA-AES256-GCM-SHA384ECDHE-ECDSA-AES256-SHAECDHE-ECDSA-AES256-SHA384ECDHE-ECDSA-CHACHA20-POLY1305ECDHE-RSA-AES128-GCM-SHA256ECDHE-RSA-AES128-SHAECDHE-RSA-AES128-SHA256ECDHE-RSA-AES256-GCM-SHA384ECDHE-RSA-AES256-SHAECDHE-RSA-AES256-SHA384ECDHE-RSA-CHACHA20-POLY1305 |
| TLS minimum version 1.2, medium security | TLSv1.2 | AES128-CCMAES128-CCM8AES128-GCM-SHA256AES128-SHA256AES256-CCMAES256-CCM8AES256-GCM-SHA384AES256-SHA256ECDHE-ECDSA-AES128-CCMECDHE-ECDSA-AES128-CCM8ECDHE-ECDSA-AES128-GCM-SHA256ECDHE-ECDSA-AES128-SHAECDHE-ECDSA-AES128-SHA256ECDHE-ECDSA-AES256-CCMECDHE-ECDSA-AES256-CCM8ECDHE-ECDSA-AES256-GCM-SHA384ECDHE-ECDSA-AES256-SHAECDHE-ECDSA-AES256-SHA384ECDHE-ECDSA-CHACHA20-POLY1305ECDHE-RSA-AES128-GCM-SHA256ECDHE-RSA-AES128-SHAECDHE-RSA-AES128-SHA256ECDHE-RSA-AES256-GCM-SHA384ECDHE-RSA-AES256-SHAECDHE-RSA-AES256-SHA384ECDHE-RSA-CHACHA20-POLY1305 |
| TLS minimum version 1.1, medium security | TLSv1.1 | AES128-CCMAES128-CCM8AES128-GCM-SHA256AES128-SHA256AES256-CCMAES256-CCM8AES256-GCM-SHA384AES256-SHA256ECDHE-ECDSA-AES128-CCMECDHE-ECDSA-AES128-CCM8ECDHE-ECDSA-AES128-GCM-SHA256ECDHE-ECDSA-AES128-SHAECDHE-ECDSA-AES128-SHA256ECDHE-ECDSA-AES256-CCMECDHE-ECDSA-AES256-CCM8ECDHE-ECDSA-AES256-GCM-SHA384ECDHE-ECDSA-AES256-SHAECDHE-ECDSA-AES256-SHA384ECDHE-ECDSA-CHACHA20-POLY1305ECDHE-RSA-AES128-GCM-SHA256ECDHE-RSA-AES128-SHAECDHE-RSA-AES128-SHA256ECDHE-RSA-AES256-GCM-SHA384ECDHE-RSA-AES256-SHAECDHE-RSA-AES256-SHA384ECDHE-RSA-CHACHA20-POLY1305 |
| TLS minimum version 1.0, medium security | TLSv1 | AES128-CCMAES128-CCM8AES128-GCM-SHA256AES128-SHA256AES256-CCMAES256-CCM8AES256-GCM-SHA384AES256-SHA256ECDHE-ECDSA-AES128-CCMECDHE-ECDSA-AES128-CCM8ECDHE-ECDSA-AES128-GCM-SHA256ECDHE-ECDSA-AES128-SHAECDHE-ECDSA-AES128-SHA256ECDHE-ECDSA-AES256-CCMECDHE-ECDSA-AES256-CCM8ECDHE-ECDSA-AES256-GCM-SHA384ECDHE-ECDSA-AES256-SHAECDHE-ECDSA-AES256-SHA384ECDHE-ECDSA-CHACHA20-POLY1305ECDHE-RSA-AES128-GCM-SHA256ECDHE-RSA-AES128-SHAECDHE-RSA-AES128-SHA256ECDHE-RSA-AES256-GCM-SHA384ECDHE-RSA-AES256-SHAECDHE-RSA-AES256-SHA384ECDHE-RSA-CHACHA20-POLY1305 |
| Only TLS version change, minimum version 1.2 | TLSv1.2 | - |
| Only TLS version change, minimum version 1.1 | TLSv1.1 | - |
Differences between predefined policies, see the following table
| Minimum TLS version 1.2, high security | Minimum TLS version 1.1, high security | Minimum TLS version 1.0, high security | Minimum TLS version 1.2, medium security | Minimum TLS version 1.1, medium security | Minimum TLS version 1.0, medium security | |
|---|---|---|---|---|---|---|
| ECDHE-ECDSA-AES128-CCM | ✔ | ✔ | ✔ | ✔ | ✔ | ✔ |
| ECDHE-ECDSA-AES128-CCM8 | ✔ | ✔ | ✔ | ✔ | ✔ | ✔ |
| ECDHE-ECDSA-AES128-GCM-SHA256 | ✔ | ✔ | ✔ | ✔ | ✔ | ✔ |
| ECDHE-ECDSA-AES128-SHA | ✔ | ✔ | ✔ | ✔ | ✔ | ✔ |
| ECDHE-ECDSA-AES128-SHA256 | ✔ | ✔ | ✔ | ✔ | ✔ | ✔ |
| ECDHE-ECDSA-AES256-CCM | ✔ | ✔ | ✔ | ✔ | ✔ | ✔ |
| ECDHE-ECDSA-AES256-CCM8 | ✔ | ✔ | ✔ | ✔ | ✔ | ✔ |
| ECDHE-ECDSA-AES256-GCM-SHA384 | ✔ | ✔ | ✔ | ✔ | ✔ | ✔ |
| ECDHE-ECDSA-AES256-SHA | ✔ | ✔ | ✔ | ✔ | ✔ | ✔ |
| ECDHE-ECDSA-AES256-SHA384 | ✔ | ✔ | ✔ | ✔ | ✔ | ✔ |
| ECDHE-ECDSA-CHACHA20-POLY1305 | ✔ | ✔ | ✔ | ✔ | ✔ | ✔ |
| ECDHE-RSA-AES128-GCM-SHA256 | ✔ | ✔ | ✔ | ✔ | ✔ | ✔ |
| ECDHE-RSA-AES128-SHA | ✔ | ✔ | ✔ | ✔ | ✔ | ✔ |
| ECDHE-RSA-AES128-SHA256 | ✔ | ✔ | ✔ | ✔ | ✔ | ✔ |
| ECDHE-RSA-AES256-GCM-SHA384 | ✔ | ✔ | ✔ | ✔ | ✔ | ✔ |
| ECDHE-RSA-AES256-SHA | ✔ | ✔ | ✔ | ✔ | ✔ | ✔ |
| ECDHE-RSA-AES256-SHA384 | ✔ | ✔ | ✔ | ✔ | ✔ | ✔ |
| ECDHE-RSA-CHACHA20-POLY1305 | ✔ | ✔ | ✔ | ✔ | ✔ | ✔ |
| AES128-CCM | ✔ | ✔ | ✔ | |||
| AES128-CCM8 | ✔ | ✔ | ✔ | |||
| AES128-GCM-SHA256 | ✔ | ✔ | ✔ | |||
| AES128-SHA256 | ✔ | ✔ | ✔ | |||
| AES256-CCM | ✔ | ✔ | ✔ | |||
| AES256-CCM8 | ✔ | ✔ | ✔ | |||
| AES256-GCM-SHA384 | ✔ | ✔ | ✔ | |||
| AES256-SHA256 | ✔ | ✔ | ✔ |
Explanation:
- The maximum protocol version of TLS can support up to TLSv1.3. If using TLSv1.3 for negotiation, the corresponding default encryption suite is:
- TLS_AES_128_GCM_SHA256
- TLS_AES_256_GCM_SHA384
- TLS_CHACHA20_POLY1305_SHA256
- In addition to the six predefined policies in the table above, there are the following two. Their encryption algorithm suite is consistent with the native policy:
- security-tls12o, only TLS version change, minimum version 1.2
- security-tls11o, only TLS version change, minimum version 1.1
- The encryption suite supported by the high-security policy in the predefined policies is in the ALB environment, which is equivalent to the syntax.
ALL:!NULL:!aNULL:!DSS:!RC4:!RC2:!EXP:!LOW:!SSLv3:!CAMELLIA:!ARIA:!3DES:!DH:!DHE:!RSA- The encryption suite supported by the high-security policy in the predefined policies is in the ALB environment, which is equivalent to the syntax.
ALL:!NULL:!aNULL:!DSS:!RC4:!RC2:!EXP:!LOW:!SSLv3:!CAMELLIA:!ARIA:!3DES:!DH:!DHECustom Policies
You can define the policy you need by combining the minimum version of the TLS protocol and the encryption algorithm suite.
Create Custom Policy
- Log in to the ALB Console.
- Select Security Policy Management.
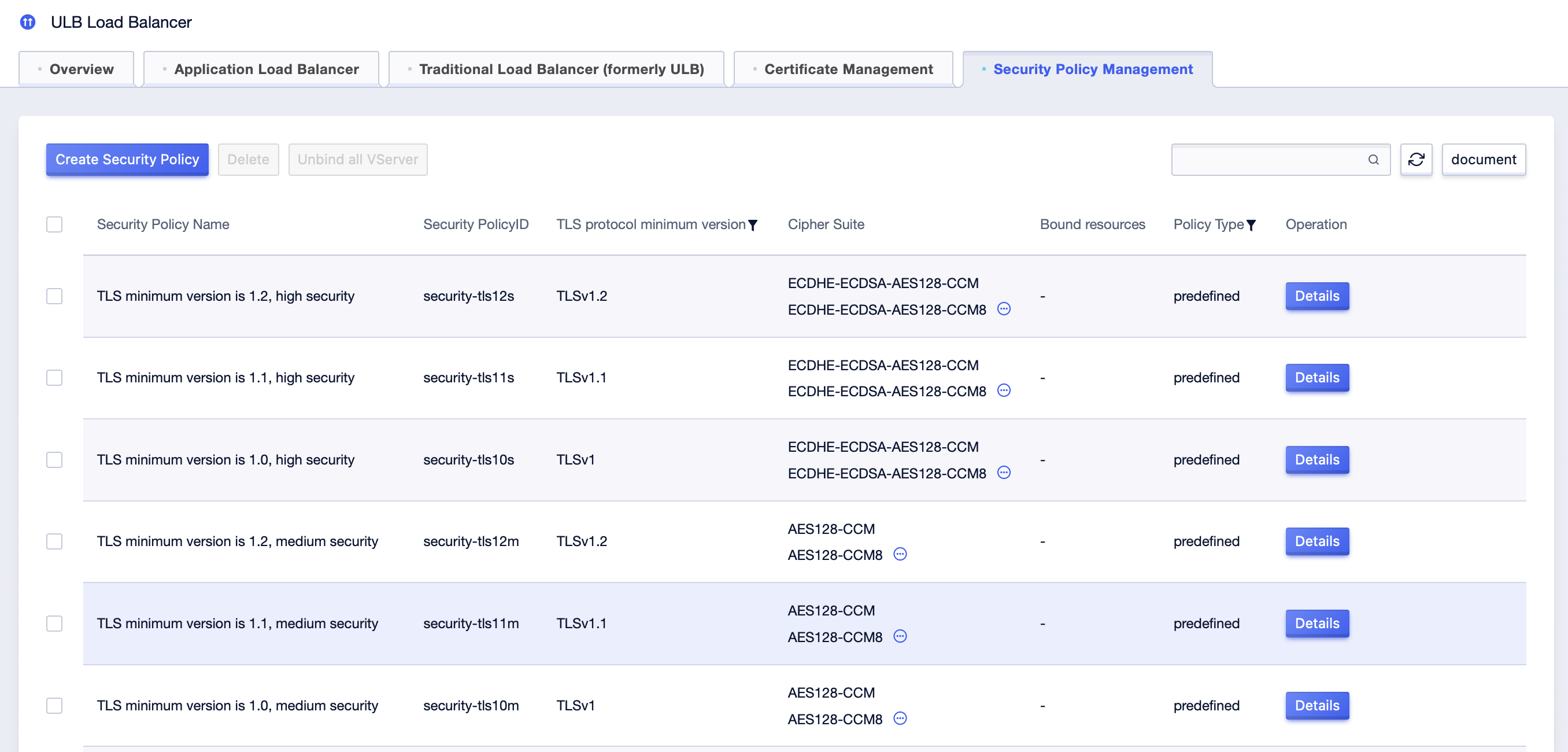
3. On the Security Policy List page, click Create Security Policy.
- In the Create Security Policy dialog, complete the following parameter configuration, and click OK after the configuration is complete.
| Configuration Item | Description |
|---|---|
| Name | Enter a custom policy name. |
| TLS protocol minimum version | The minimum version of the TLS protocol, a required item, the optional TLS versions are TLSv1, TLSv1.1, TLSv1.2 |
| Cryptographic algorithm suite | Select the encryption algorithm suite supported by the TLS version. |
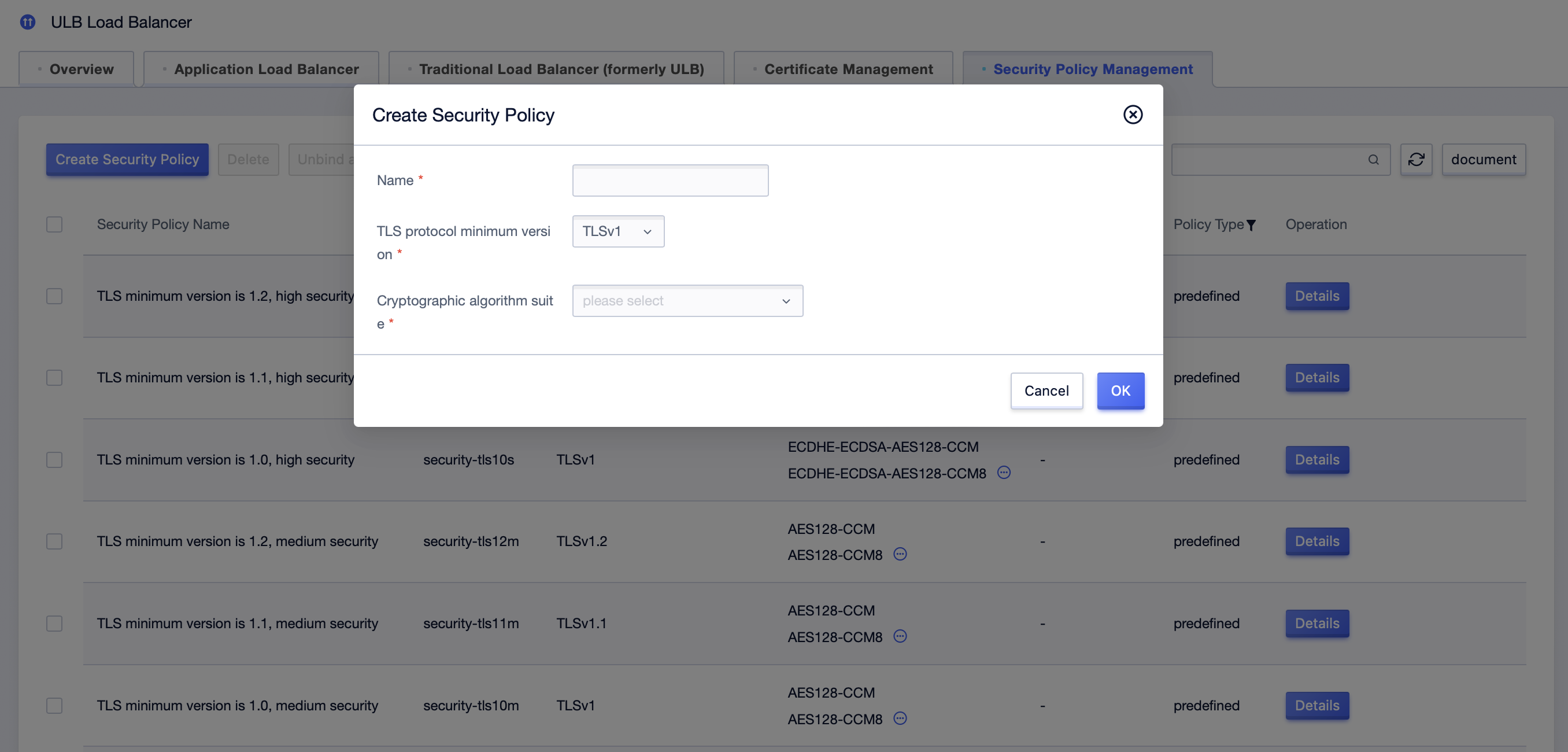
5. Once the custom policy is created, you can configure the custom policy in the advanced settings when creating HTTPS listening.
Delete Single Custom Security Policy
- Log in to the ALB Console.
- Select Security Policy Management.

3. On the Security Policy List page, select the custom security policy you want to delete and click Delete.
-
In the second confirmation pop-up window, confirm whether it is the security policy you want to delete.
-
Click “Confirm” to complete the deletion.
Bulk Delete Custom Security Policies
- Log in to the ALB Console.
- Select Security Policy Management.
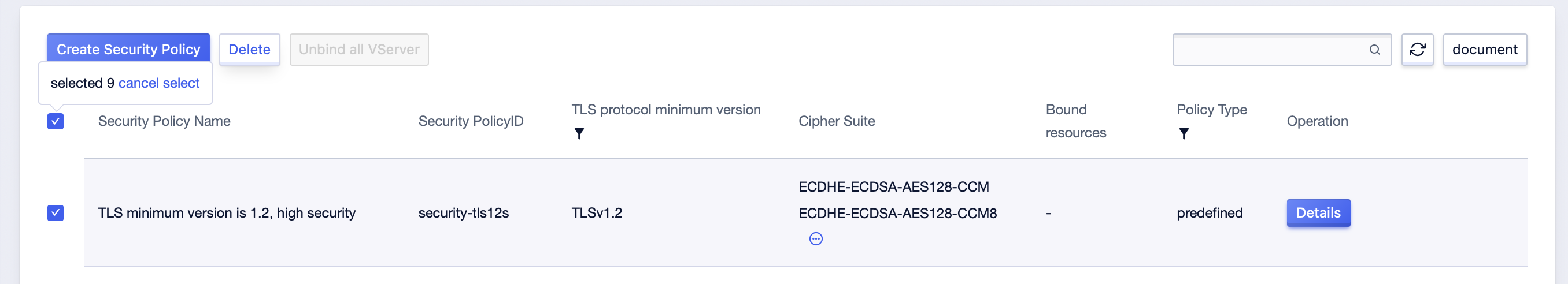
-
On the Security Policy List page, batch select the checkboxes on the left of the security policies you want to delete, and click “Delete” above.
-
In the second confirmation pop-up window, confirm whether they are the security policies you want to delete.
-
Click Confirm to complete the deletion.
If you want to delete a custom policy, you must first unbind VServer before you can delete it.
Edit Custom Security Policies
You can update custom security policies as needed.
-
Log in to the ALB Console.
-
Select Security Policy Management.
-
On the Security Policy List page, select the custom policy you want to edit and click “Edit” in the operation bar.

4. Set the following information in the “Edit Security Group Policy” dialog box:
| Configuration Item | Description |
|---|---|
| Name | Enter a custom policy name. |
| TLS protocol minimum version | The minimum version of the TLS protocol, a required item. The optional TLS versions are TLSv1, TLSv1.1, TLSv1.2. |
| Cryptographic algorithm suite | Select the encryption algorithm suite supported by the TLS version. |
- Click OK after the modification to complete the editing operation.