Anti-Leech
US3 storage spaces support configuring anti-leech policies. Once enabled, you can set up blacklists and whitelists for access sources to prevent US3 resources from being stolen by others or having public network traffic hijacked, thus avoiding unnecessary losses.
Set up Anti-Leech
-
Log in to the US3 Object Storage Console.
-
Click Single Region Space Management, then click the target Bucket.
-
In the top navigation bar, select Basic Settings, turn on the Anti-Leech switch, and then click Edit to enter an editable state:
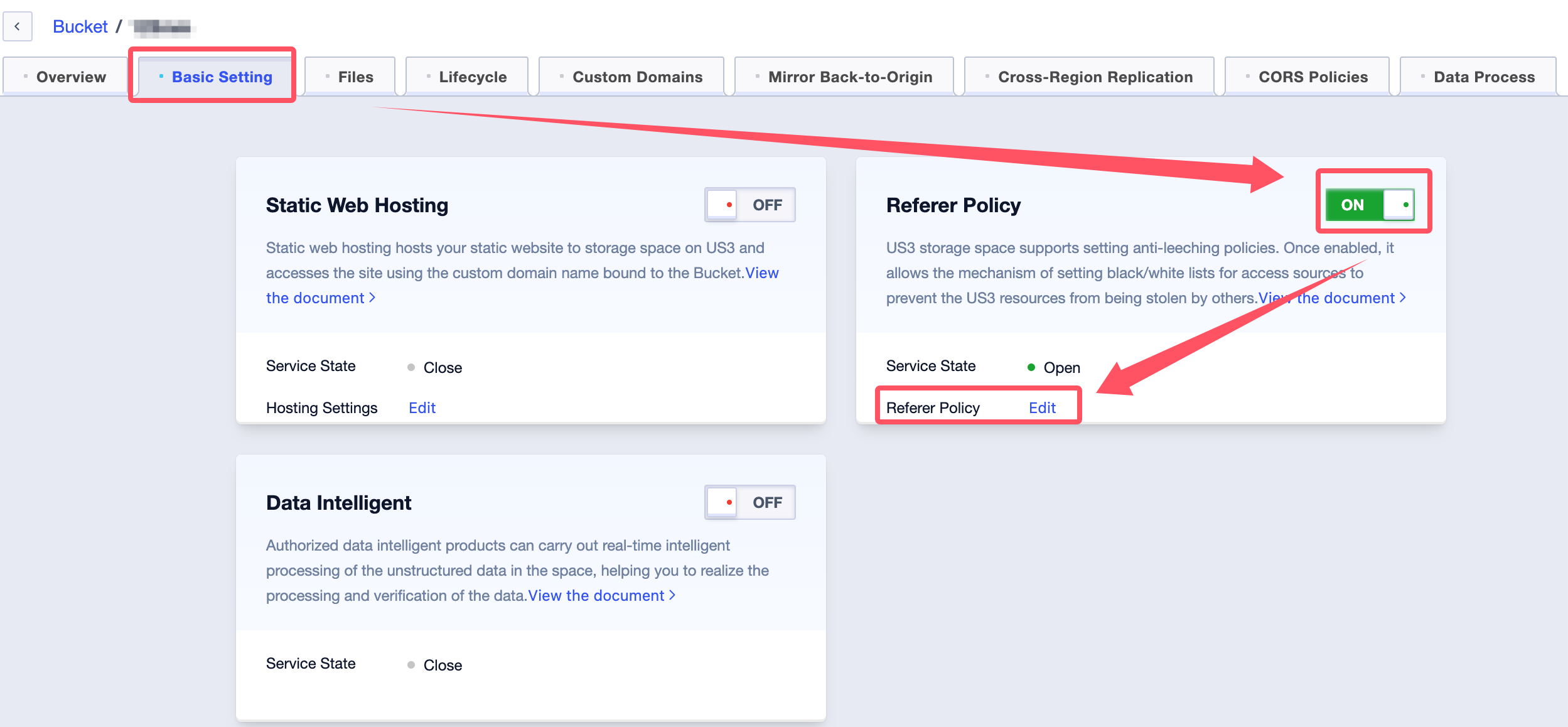
-
Configure according to actual needs. The explanations of configuration items are as follows:
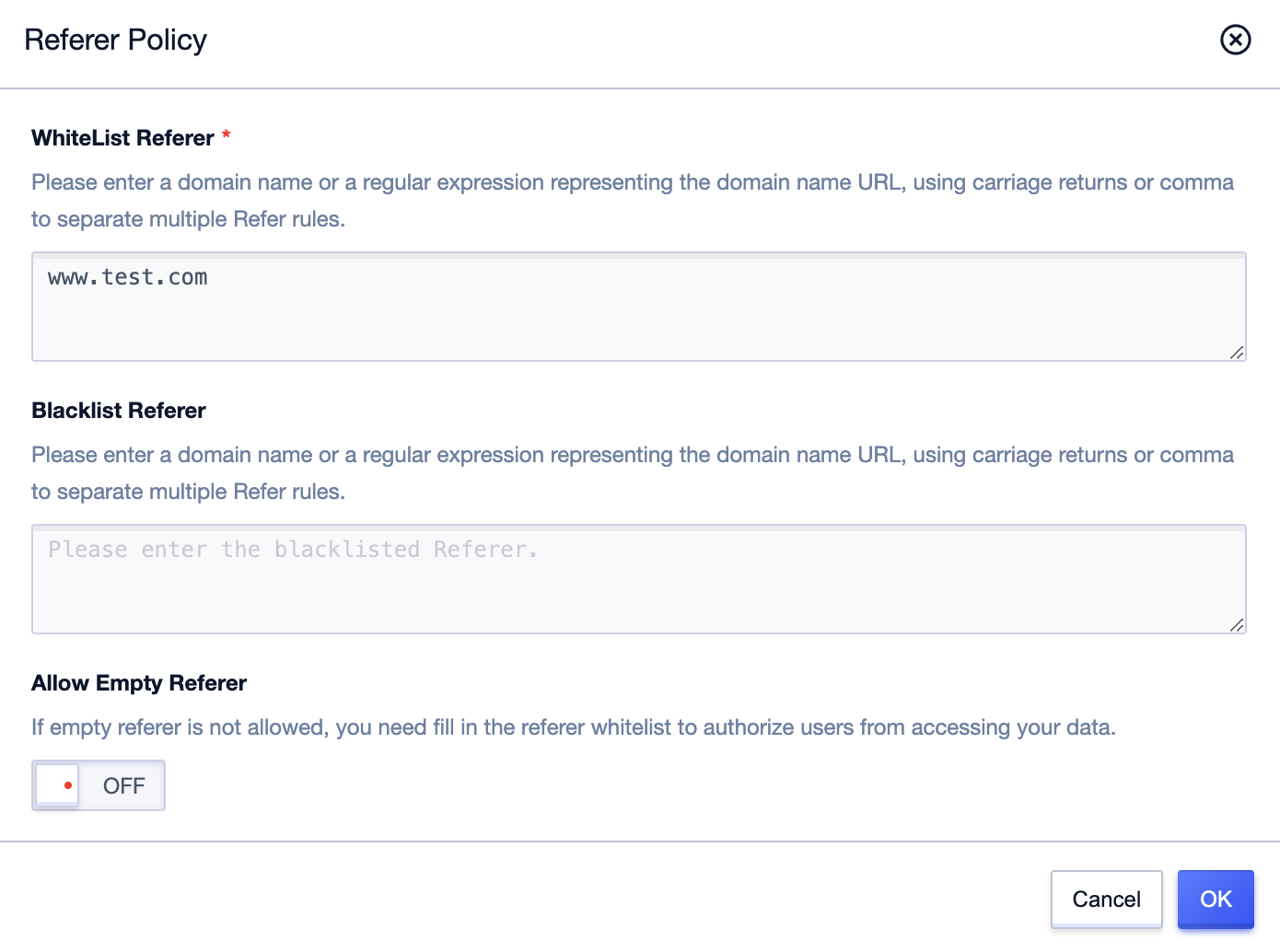
-
Whitelist Referer: Allow domain names in the list to access the default access address of the storage space. If the domain name outside the list accesses the default access address of the bucket, it will return 403.
-
Blacklist Referer: Deny domain names in the list to access the default access address of the storage space. If the domain name in the list accesses the default access address of the bucket, it will return 403.
Please enter the domain name or the regular expression representing the domain name URL, separated by carriage return or English comma for multiple Refer rules.
-
Allow Empty Referer:
-
Yes: Allows requests without a Referer or with an empty Referer.
-
No: Requires requests to carry a Referer and the Referer value cannot be empty. After setting to disallow empty Referer, only requests containing the Referer field in the HTTP or HTTPS header can access US3 object storage resources.
-
- Click Confirm to complete the anti-leech setting.