SSO
We support SSO (Single Sign-On), also known as federated identity login, based on SAML 2.0. This document explains how enterprises can implement SSO with XXXCloud using their own identity systems.
Basic Concepts
- Identity Provider (IdP): An IAM entity that contains metadata about the external identity provider and provides identity management services.
- Enterprise Local IdP: Microsoft Active Directory Federation Service (AD FS), Shibboleth, etc.
- Cloud IdP: XXXCloud Application Identity Service, Azure AD, Google Workspace, Okta, OneLogin, etc.
- Service Provider (SP): An application that uses IdP’s identity management function to provide specific services to users. The SP uses the user information provided by IdP.
- Security Assertion Markup Language (SAML 2.0): A standard protocol for implementing enterprise-level user identity authentication. It is one of the technical implementations for connectivity between SP and IdP. SAML 2.0 is now a de facto standard for implementing enterprise-level SSO.
- SAML assertion: The core element in the SAML protocol that describes authentication requests and responses. For example, user specific attributes will be included in the assertion of the authentication response.
- Trust: The trusting mechanism established between the SP and IdP, usually implemented by public and private keys. The SP obtains the SAML metadata of IdP in a trusted way, the metadata contains the signature validation public key issued by IdP’s SAML assertion. The SP then uses the public key to verify the integrity of the assertion.
- Verification fingerprint: In order to prevent the Issuer URL from being maliciously hijacked or tampered, you need to configure the verification fingerprint generated by the external IdP’s HTTPS CA certificate. XXXCloud will help you calculate this verification fingerprint automatically. But it is suggested that you calculate it once locally (for example, using OpenSSL to calculate the fingerprint) and compare it with the fingerprint calculated by XXXCloud. If a discrepancy is found, it means that the Issuer URL may have been attacked. Please be sure to confirm again and fill in the correct fingerprint.
SAML Configuration of XXXCloud SP
Operation Steps
Go to Authority Management — SSO Management. This feature is disabled by default; XXXCloud users can log in with passwords, and all SSO settings are inactive.
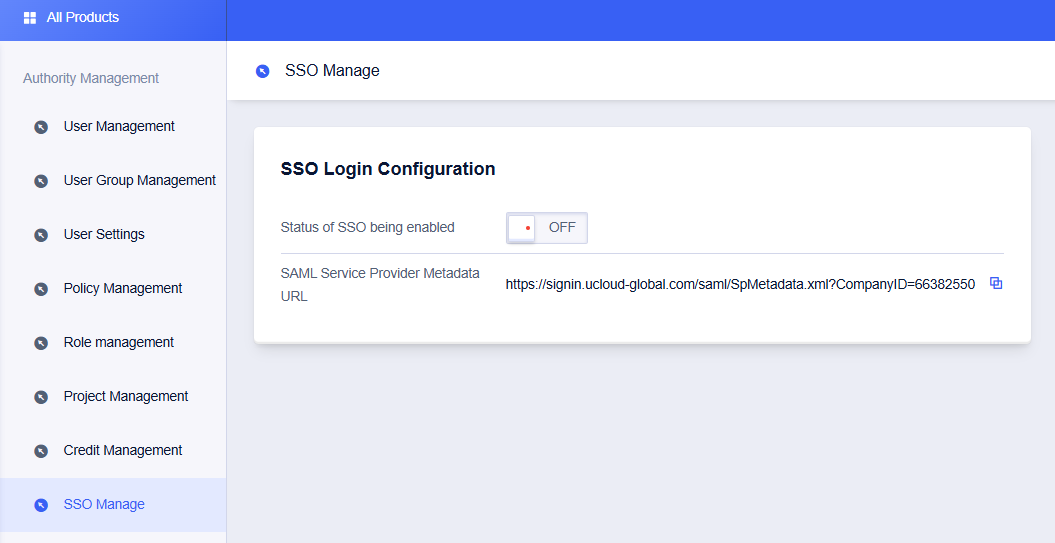
If you choose to enable this function, the password login method for sub-users will be closed and unifiedly redirected to the enterprise IdP for identity authentication. If it is closed again, the user password login method will be automatically restored.
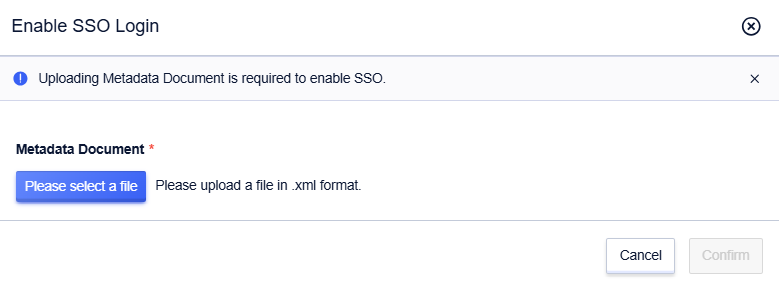
Metadata document: Click to upload the file, upload the metadata document provided by the enterprise IdP.
Note: The metadata document is provided by the enterprise IdP, usually in XML format, containing the IdP’s login service address and X.509 public key certificate (used to verify the validity of the SAML assertion issued by the IdP).
Click to enable the function, and upload the metadata file.
Note: This function only applies to all IAM sub-users under the account of XXXCloud, and will not affect the login of the XXXCloud master account.
Follow-up Steps
After completing the SAML configuration, create IAM users that match the enterprise IdP:
- Go to User Management — Invite Sub-users.
- Enter the username (no email is required); the system will generate a virtual email address for the sub-user.
- The sub-user will be activated immediately after the invitation is successful.
Note: After enabling SSO, if you disable the SSO feature again, you need to enable console access capability for sub-users created during the SSO-enabled period. This allows sub-users to log in using their account emails (or other methods) after SSO is disabled.
SAML Configuration for Enterprise IdP
Obtain SAML service provider metadata URL from XXXCloud.
Create a SAML SP in your enterprise IdP and configure XXXCloud as the trusted party in any of the following ways according to the actual situation.
Directly configure the XXXCloud metadata URL described in Step 1.
If your IdP does not support URL configuration, you can download the metadata file through the URL described in Step 1 and upload it to your IdP.
If your IdP does not support the uploading of metadata files, you need to manually configure the following parameters:
- Entity ID: The value of the entityID attribute of the md:EntityDescriptor element in the downloaded metadata XML.
- ACS URL: The value of the Location attribute of the md:AssertionConsumerService element in the downloaded metadata XML.
SAML Response for User SSO
In the SAML 2.0-based SSO process, after an enterprise user logs in to the IdP, the IdP generates an authentication response containing a SAML assertion in accordance with the requirements of the SAML 2.0 HTTP-POST binding. This response is automatically forwarded to XXXCloud by the browser (or program). The SAML assertion is used to confirm the user’s login status and parse the login principal. Therefore, the assertion must contain the elements required by XXXCloud; otherwise, the user’s identity cannot be confirmed, resulting in SSO failure.
SAML Response
Ensure that the SAML response sent by your IdP to XXXCloud meets the following requirements. All elements must be included; otherwise, SSO will fail.
<saml2p:Response>
<saml2:Issuer>...</saml2:Issuer>
<ds:Signature>
...
</ds:Signature>
<saml2p:Status>
...
</saml2p:Status>
<saml2:Assertion>
<saml2:Issuer>...</saml2:Issuer>
<saml2:Subject>
<saml2:NameID>${NameID}</saml2:NameID>
<saml2:SubjectConfirmation>
...
</saml2:SubjectConfirmation>
</saml2:Subject>
<saml2:Conditions>
<saml2:AudienceRestriction>
<saml2:Audience>${Audience}</saml2:Audience>
</saml2:AudienceRestriction>
</saml2:Conditions>
<saml2:AuthnStatement>
...
</saml2:AuthnStatement>
</saml2:Assertion>
</saml2p:Response> Explanation of Elements in SAML Assertion
- Common elements of the SAML 2.0 protocol
| Element | Description |
|---|---|
| Issuer | The value of Issuer must match the EntityID in the metadata file you uploaded in the user SSO settings of XXXCloud. |
| Signature | XXXCloud requires that SAML assertions must be signed to ensure that they have not been tampered with, Signature and its contained elements must include information such as the signature value and signature algorithm. |
| Subject | The Subject must contain the following elements: there is only one NameID element, which is the identity identifier of a certain IAM sub-user under the XXXCloud account. For details, please refer to the NameID element and NameID example described below. There is only one SubjectConfirmation element, which contains a SubjectConfirmationData element. The SubjectConfirmationData must have the following two properties: NotOnOrAfter: Specifies the validity period of the SAML assertion. Recipient: XXXCloud checks the value of this element to ensure that XXXCloud is the intended recipient of this assertion, its value must be https://signin.XXXCloud.cn/saml/SSO . |
| Conditions | In the Conditions element, there must be an AudienceRestriction element, which can contain one to many Audience elements, but there must be an Audience element with the value of https://signin.XXXCloud.cn/${CompanyID}/saml/SSO , where ${CompanyID} is the company ID of XXXCloud. |
Here is an example of a Subject element:
<Subject>
<NameID Format="urn:oasis:names:tc:SAML:2.0:nameid-format:persistent">Alice</NameID>
<SubjectConfirmation Method="urn:oasis:names:tc:SAML:2.0:cm:bearer">
<SubjectConfirmationData NotOnOrAfter="2019-01-01T00:01:00.000Z" Recipient="https://signin.XXXCloud.cn/saml/SSO"/>
</SubjectConfirmation>
</Subject>|Here is an example of a Conditions element:
<Conditions>
<AudienceRestriction>
<Audience>https://signin.XXXCloud.cn/${CompanyID}/saml/SSO</Audience>
</AudienceRestriction>
</Conditions>- NameID Element
XXXCloud locates an IAM sub-user using CompanyID + username. Therefore, the SAML assertion generated by the enterprise IdP must contain the sub-user’s username. XXXCloud parses the NameID element in the SAML assertion to match the username of the IAM sub-user, thereby implementing user SSO.
When configuring the SAML assertion issued by the IdP, you need to map the field corresponding to the IAM sub-user’s username to the NameID element in the SAML assertion.