Policy Management
A permissions describes the relationship between users and resources, and determines the user’s ability to access and control resources.
A policy is a collection of permissions structured through specific syntax. It consists of five components: V (version), E (effect), A (action), and R (resource). It precisely describes under what conditions a user is allowed/denied to perform specific operations on specific resources.
- V (version): The syntax version, maintained by XXXCloud. The current version of system policies is V1, which cannot be modified; custom policies will automatically generate a new version after being edited and saved.
- E (effect): The execution effect, either Allow or Deny.
- A (action): The API name(s), supporting one or multiple APIs.
- R (resource): The resource, represented by a URN (Uniform Resource Name).
XXXCloud provides two modes of permission policies:
- System policy —— Configured and managed by XXXCloud
- Custom policy —— Configured and managed by users
Policy Levels
Policies are divided into two levels based on their effective scope: Global Level and Project Level.
- Global Level: Takes effect for all services under the account, without distinguishing between projects. Global-level policies do not support project-specific authorization.
- Project Level: Takes effect for specified projects. Project-level policies support project-specific authorization.
- Note: Some system policies belong to the Global Level/Project Level, and such types cannot be created as custom policies.
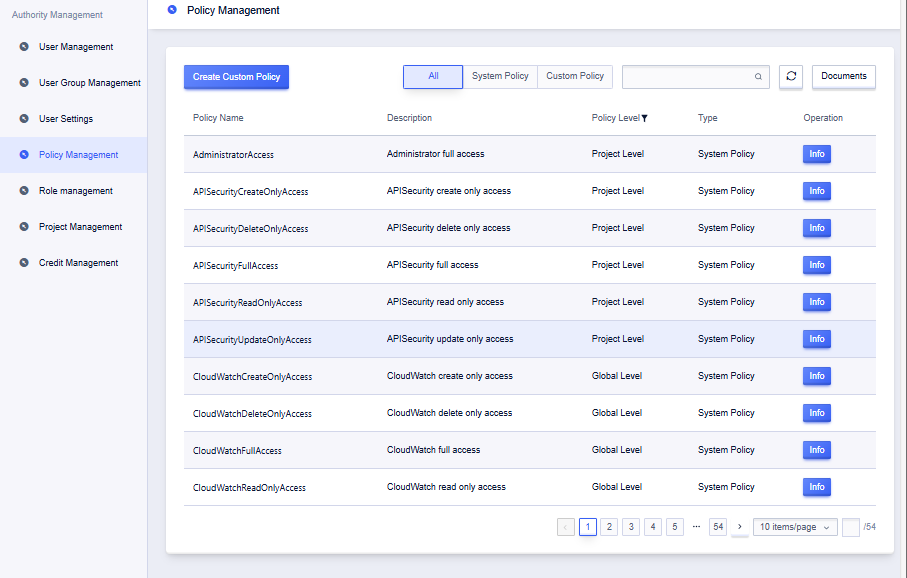
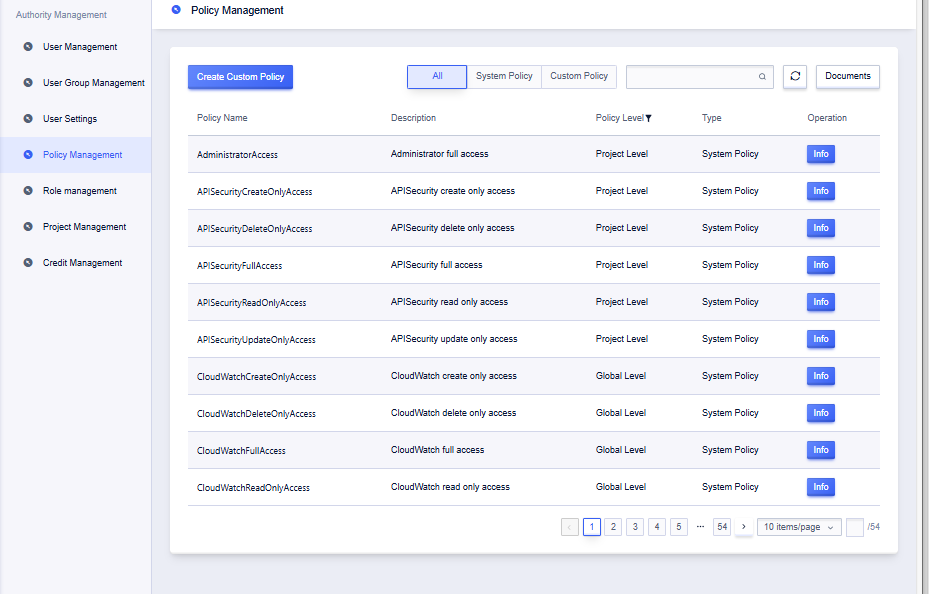
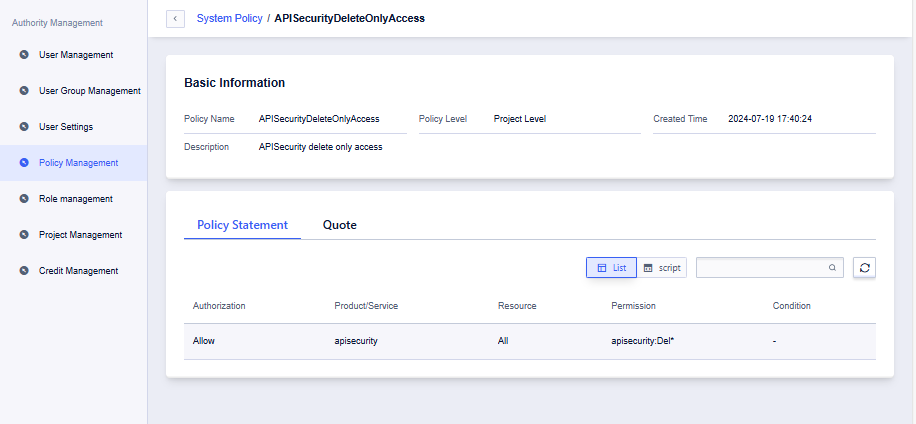
Viewing System Policies
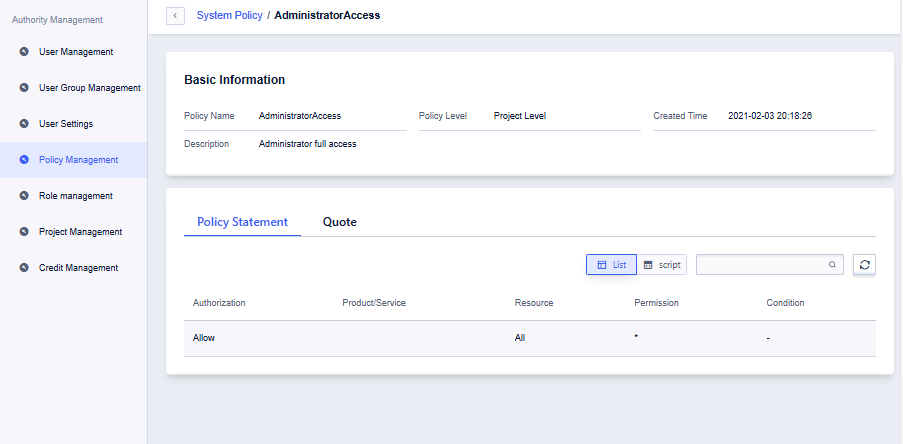
A system policy is a package of permissions grouped by operation type. Click “Details” to view the APIs included in the policy and its reference status.
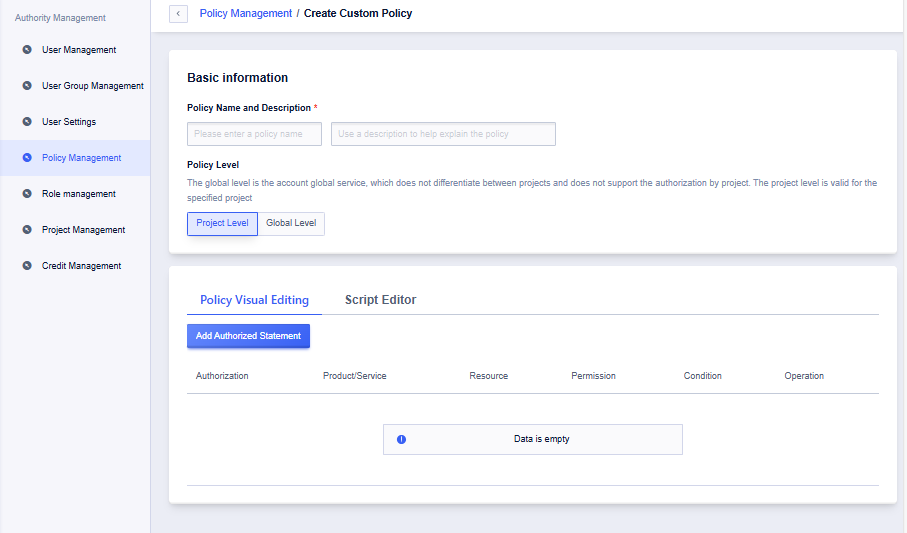
Creating Custom Policies
Custom policies can specify allowed/denied operations for specific APIs. For example, prohibiting sub-users from creating new cloud hosts.
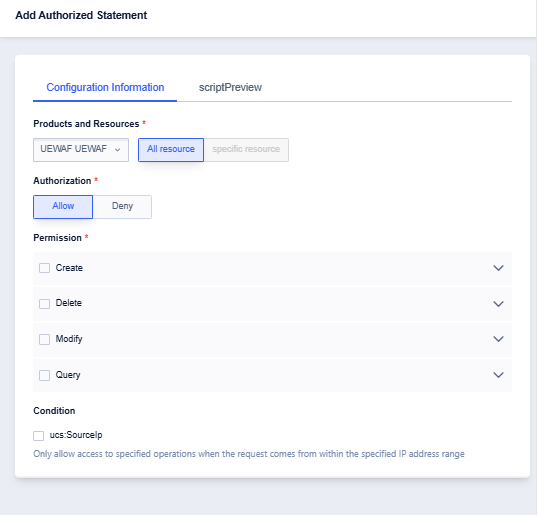
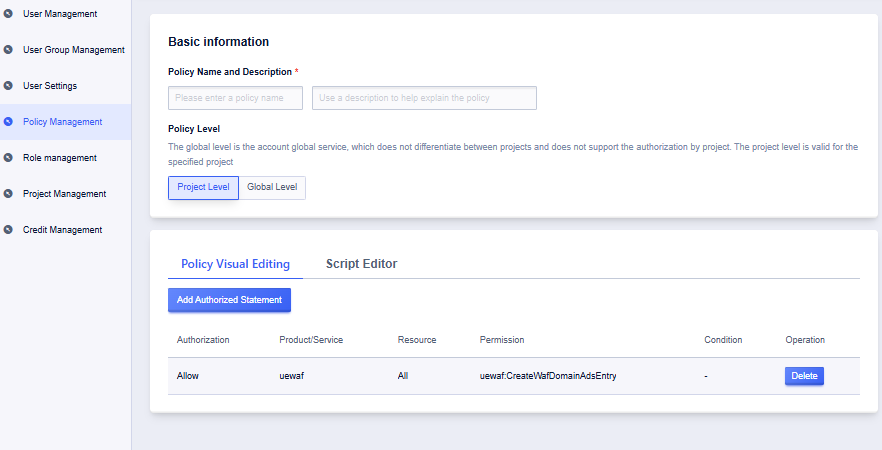
- Custom policies support editing and deleting.
- After modifying the content of a permission policy, the system will automatically generate a new version of the permission policy, which will become the current version.
- Supports setting a historical version as the current version.
Authorize Sub-Users
When authorizing, you need to distinguish between Global-Level Authorization and Project-Level Authorization:
Global-Level Policies: If all the policies you select are at the global level, these policies will be automatically applied to the global scope, and no additional effective scope needs to be specified.
Project-Level Policies: If the policies you select include project-level policies, you will have the option to select a specific effective scope. You can choose to apply the policy to a specific project or select “All Projects” (which means the policy will cover all existing projects and any future projects under your account). Please note that the “All Projects” option will affect all projects under your account, so exercise caution when selecting it.