Firewall
Recommended Firewall
To provide convenience for users, two default "Recommended Firewalls" are provided on the console, namely "Web Server Recommended" and "Non-Web Server Recommended". Apart from the "Web Server Recommended" which has the "80, 443" ports open by default, both have the "22, 3389" ports entered.
Apart from the opened ports, other ports are closed by default in the firewall rules.
The default firewall rules cannot be modified, but you can click "Copy" from the default firewall details page to create a new custom firewall with the same rules for modification.
Note:
The external network firewall only takes effect for access from the external network's Elastic IP.
Basic Firewall Function
Create Firewall
Click on 'Create Firewall' in the control panel, fill in the firewall name and remarks, and you can enter the rule addition page. On the rule addition page, click 'Add Rule', select the corresponding protocol, fill in 'Port', 'Source Address', 'Action', 'Priority' and remarks (optional), then click save to complete the most basic creation process.
Note:
'Recommended Firewall' does not support modification, but you can save the modified content from the recommended firewall as a user-defined firewall.
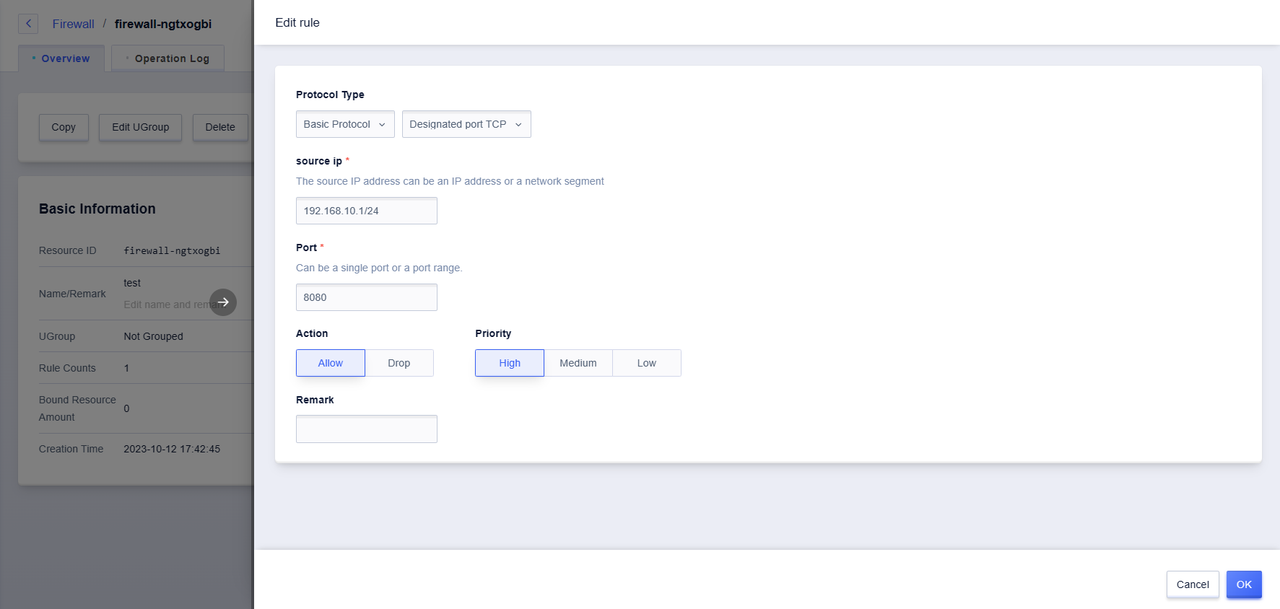
Edit Firewall Rules
Note:
By default, the firewall performs a deny action for all other accesses except for the entries that have been entered.
1.Protocol
The firewall protocol currently supports "TCP", "UDP", "ICMP" and "GRE" protocols.
2.Port
The local port visited by the source address, with a port range of [1-65535].
3.Source Address
The source address of the network data packet accessing the cloud platform host resources, supports IP addresses and network segments, and the IP address segments are separated by commas (supporting the number of IPs and network segments ≤10), such as "10.0.0.1,192.168.0.2/32".
4.Action
When the firewall takes effect, it includes "accept" and "reject" actions for handling data packets.
5.Priority
When adding rules within the firewall, the rules take effect in order of priority, and each rule includes "high", "medium", and "low" levels.
6.Remarks (optional)
You can add remarks to each rule, which is convenient for rule management and search.
- Firewall Rule Restrictions:
The firewall does not support duplicate rules. If the protocol, port, source address, and action are duplicated, it is judged as a rule duplication. Duplicate rules will cause operation errors.
If there are already duplicate rules, refer to the following solutions:
Delete all duplicate rules at the same time and resubmit the request.

Click on the dropdown box under "Quick Rules", you can see various commonly used protocols.
Protocol description:
- Basic protocols include:
(1) Specified TCP: User-defined TCP protocol port
(2) Specified UDP: User-defined UDP protocol port
(3) All-port TCP: All TCP ports
(4) All-port UDP: All UDP ports
(5) GRE: GRE protocol
(6) ICMP: ICMP protocol - Shortcut rules include:
(1) FTP: TCP port 21
(2) HTTP: TCP port 80
(3) HTTPS: TCP port 443
(4) PING: ICMP protocol
(5) OpenVPN: UDP port 1194
(6) PPTP: TCP port 1723
(7) RDP: TCP port 3389
(8) SSH: TCP port 22
Delete Firewall Rule
Firewall rules support single rule deletion, as well as batch deletion.
Note:
At least one firewall rule needs to be retained, as the "Delete" button is unavailable when all are selected.
Copy Firewall
The firewall replication can replicate all rule contents of the firewall except for its own properties, which is suitable for adding new rules based on the original firewall.
Batch Management of Bound Resources
Enter the "Resource Overview" interface, you can batch modify the firewall for the cloud host resources that have already been bound to the selected firewall.
- Click the Edit Firewall button
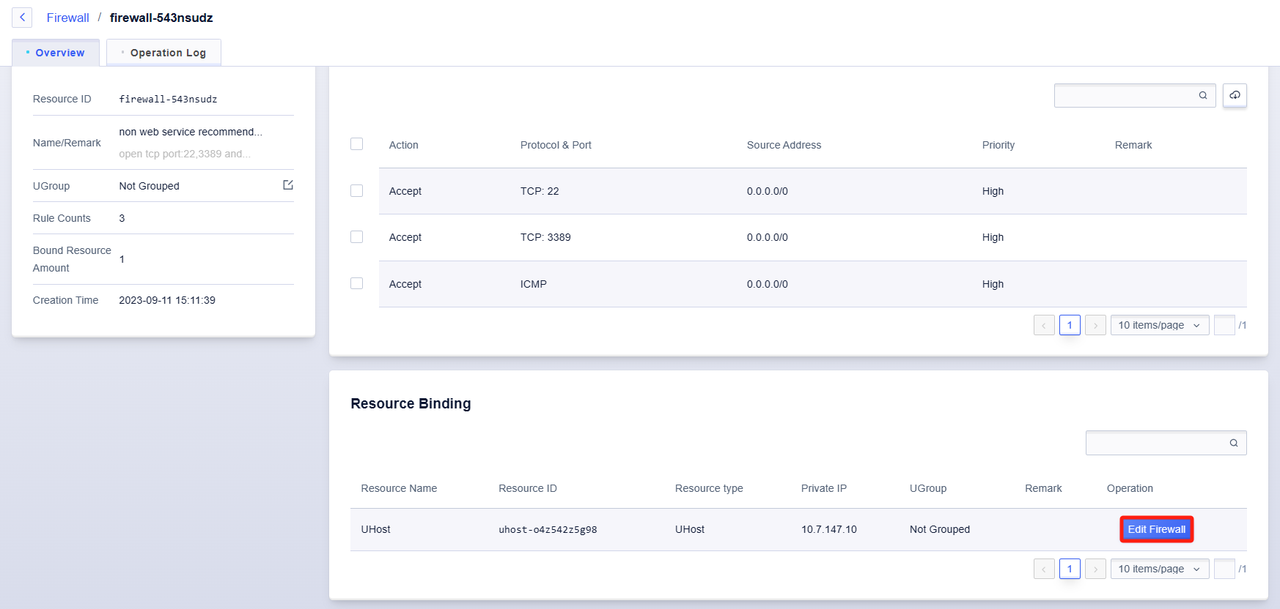
- Select the firewall that needs to be replaced
